With the Red Hat OpenShift 4.15 release, the shared resource CSI Driver operator feature (in Tech Preview) allows for sharing secrets across namespaces. This addresses a common developer request, enabling the creation of secrets in one place and seamless sharing across projects. This is particularly handy for efficiently managing frequently accessed services like Messaging layer, Databases, and Registries.
In this article, we'll dive into the technical aspects of leveraging this feature, optimizing your OpenShift workflow for enhanced secret management. We will walk through a simple Spring Boot example, which will read a secret from a mount, and display the contents. This secret will be created as a sharedSecret on another namespace.
Prerequisites
As a cluster admin, to enable Tech Preview features, enable feature gate.
Create the namespace and secret:
$ oc new-project namespace1$ oc create secret generic greeting-secret --from-literal greeting-message="Secret message from Namespace1."Create the SharedSecret:
$ oc apply -f - <<EOF
apiVersion: sharedresource.openshift.io/v1alpha1
kind: SharedSecret
metadata:
name: my-share
spec:
secretRef:
name: greeting-secret
namespace: namespace1
EOF
sharedsecret.sharedresource.openshift.io/my-share configuredCreate the application namespace:
$ oc new-project namespaceCreate Role and RoleBinding to access the shared secret:
$ oc apply -f - <<EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: shared-resource-my-share
namespace: namespace2
rules:
- apiGroups:
- sharedresource.openshift.io
resources:
- sharedsecrets
resourceNames:
- my-share
verbs:
- use
EOF
role.rbac.authorization.k8s.io/shared-resource-my-share created$ oc create rolebinding shared-resource-my-share --role=shared-resource-my-share --serviceaccount=namespace2:builder
rolebinding.rbac.authorization.k8s.io/shared-resource-my-share createdDeploy application using Source-to-Image (S2I)
Navigate to the +Add tab, select the Import from Git option, and provide the following URL: https://github.com/bharathi-tenneti/devfile-sample-java-springboot-basic.git
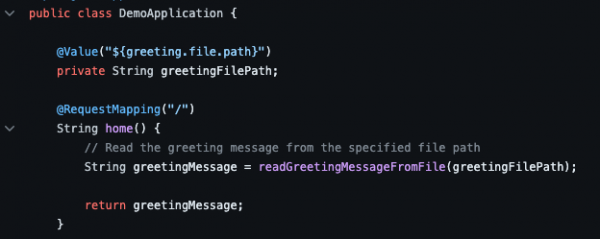
The application is configured to look for a path to read the message coming from the secret and display it, as shown in Figure 1.
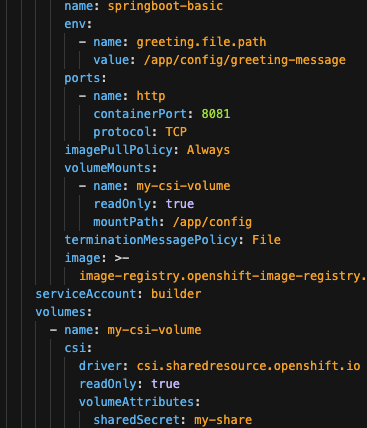
Edit the deployment YAML to mount the shared secret from CSI volumes, as illustrated in Figure 2.
Test the application
Test the application:
$ curl springboot-basic-namespace2.apps.cluster-tcbgg.dynamic.opentlc.com
Secret message from Namespace1.In a similar way, ConfigMaps can be shared across OpenShift namespaces as well.