Edge computing has become a major part of our current technology ecosystem, from your neighborhood Dunkin’ Donuts to the watch on your wrist. In fact, Gartner estimates that “about 10% of enterprise-generated data is created and processed outside a traditional centralized data center or cloud” (essentially, edge). And those applications appear poised to expand: according to Gartner, that number will grow to 75% by 2025.
Still, edge computing remains a niche topic that many people are unfamiliar with. This article highlights five facts for developers to know about edge.
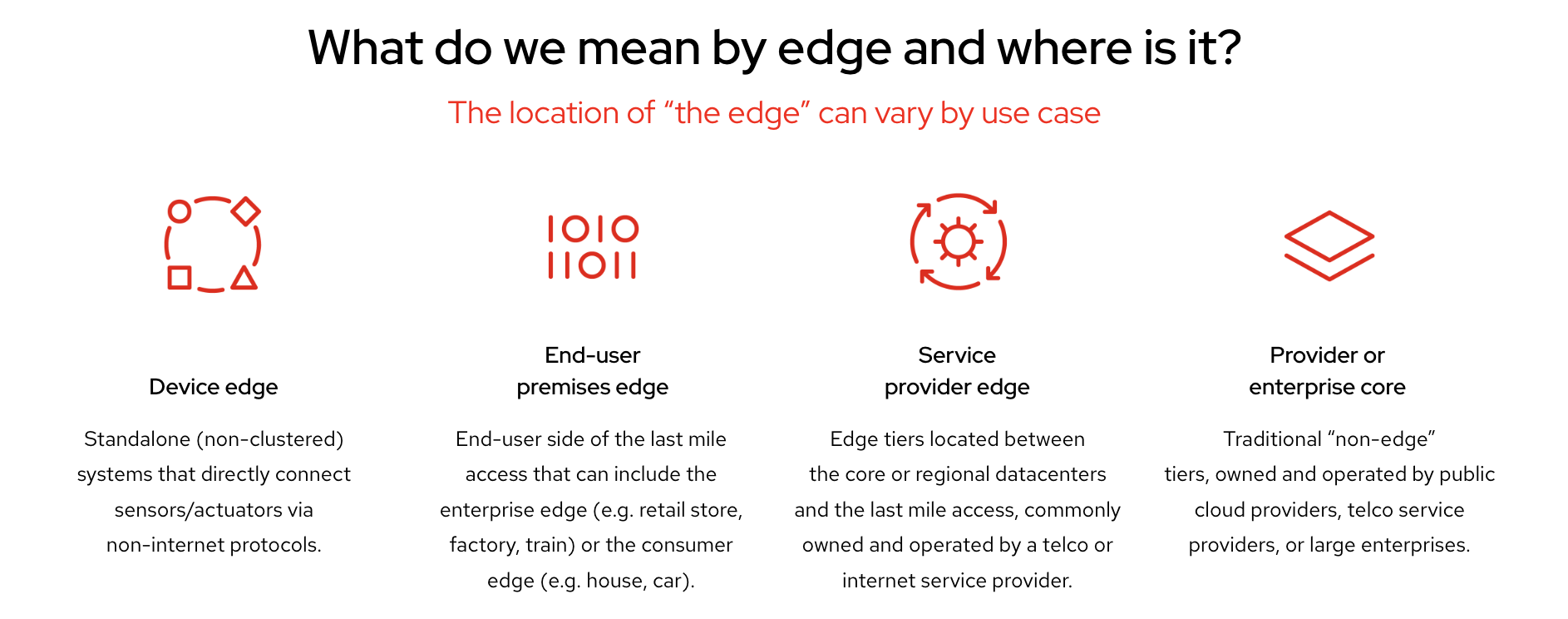
1. Edge is everywhere
Here are some examples of different edge computing use cases (also shown in Figure 1):
- A device edge: Standalone (non-clustered) systems that directly connect sensors via non-Internet protocols—for example, a coffee shop or your local restaurant.
- End-user premises edge: This includes retail stores, trains, or even a house or car.
- Service provider edge: Edge tiers located between the core or regional datacenters and the last mile access are commonly owned and operated by a telco or Internet service provider.
- Provider or enterprise core: Traditional “non-edge” tiers owned and operated by public cloud providers, telco service providers, or large enterprises.
To see more use cases and how companies are using edge technologies, refer to this article from Red Hat.
Edge, at its simplest, is localized data processing at the place at or near where it’s created. By placing computing services closer to these locations, users benefit from faster, more reliable services, and companies can benefit from the flexibility of hybrid cloud computing.
To go more in-depth about what edge computing entails, read this article: What is edge computing?
2. Edge is growing exponentially
Edge computing is becoming more relevant to the requirements of current organizations, companies, and the public sector trying to develop applications in remote locations and enabling localized computing capabilities where needed. Gartner also insists in their 2022 document The Distributed Enterprise Drives Computing to the Edge that “enterprises need to make plans to capture the opportunities and prepare for the challenges of managing data in edge environments.”
Locations that can benefit from the edge model include disaster zones where the deployment of servers and computer power is needed to communicate and spread resources or cruise ships that need to provide services. Even the International Space Station needs to run software, process data, and communicate with others. To learn more, see Edge computing in action: Space.
3. You can leverage your cloud development knowledge for edge
Currently, edge technology may seem like a niche field, but translating your own knowledge of cloud to edge is easier than you think. Practices that have been developed in the cloud-based space over the last 20 years can be adapted and used for edge computing development.
One example of this includes one of the most commonly known languages, Java. While old versions of Java had known limitations, new frameworks like Quarkus and Java Virtual Machines like GraalVM allow existing cloud developers to reuse their current knowledge. Java has consistently been in the top three programming languages on the TIOBE ratings for the past eighteen years.
Other aspects that can be used in both cloud and edge include:
- DevSecOps, which focuses on software-defined life cycles and emphasizes automation and security. Applications can be deployed consistently and with quality.
- Container images. Developers can easily upgrade and update code on devices running smart advertisements.
With the Red Hat build of Quarkus, you can deploy, create, and develop applications that are serverless friendly and lightweight in resources. Those applications can then be packaged as containers to be run with Podman and Red Hat Device Edge, or as native builds for Red Hat Enterprise Linux for edge.
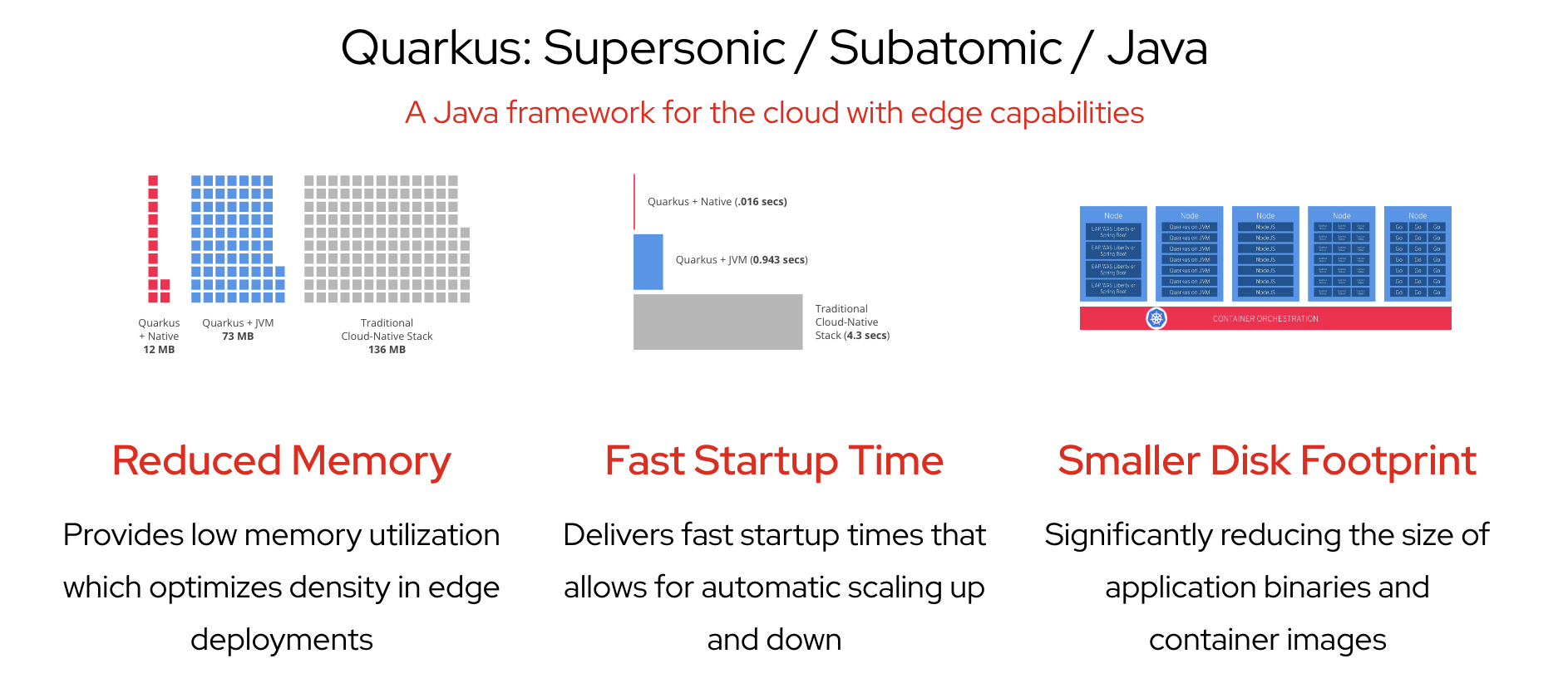
The benefits of this Quarkus Java framework with edge capabilities (illustrated in Figure 2) include:
- Reduced memory utilization.
- Fast start-up time, which allows for automatic scaling up and down.
- Smaller disk footprint, which significantly reduces the size of application binaries and container images.
With edge-to-cloud pipelines, you can implement scalable, security-focused event-driven data architecture to allow better visibility and real-time decision-making at the network edge. Companies like Red Hat provide a robust set of solutions to create lightweight applications, process and store data on-site, as well as use business rules and algorithms to lead decision-making at edge sites.
4. Applications at the edge boost performance and reduce latency
We frequently host data on centralized platforms, which introduces latency when consumers attempt to access it from distant places. Requesting data from these data centers in unreliable or spotty internet locations can be slow. This problem is resolved by edge computing, which keeps data on edge servers for easy access.
Because data can be retrieved directly from the endpoints rather than from a remote centralized data center, then sent back to the endpoints, organizations may avoid concerns with speed and connectivity thanks to edge computing. Applications can continue to be improved for better performance and a better user experience by cutting down on the distance they have to travel to retrieve data from a data center.
Additionally, keeping data at the edge lowers operating expenses. For enterprises worldwide, using cloud services to host data, especially large volumes of data, is extremely expensive. Organizations spend more money the more data is moved on centralized hosting providers. It becomes crucial to understand what data has to be transported from the production location to these centers.
However, because there is less need to transfer data to the cloud when using edge computing, businesses can pay less on operational expenditures. The amount of bandwidth required to handle the data transfer is also decreased because data is classified, cleaned, and compressed in the same site where it is generated.
5. Edge enhances privacy protections and data security
In the world of IT, data security and privacy protection are hot topics. Because data is handled locally rather than coming from centralized servers, edge computing offers a higher level of data security and privacy protection.
This in no way implies, however, that edge computing devices are not at all vulnerable. In no way. It merely implies that there is less data to be processed at the edge, indicating that there isn't a huge amount of data that can be exploited by hackers.
In other words, when data kept on centralized servers are breached, privacy can be readily jeopardized because they have more detailed information about individuals, places, and events. Since edge computing only generates, processes, and analyzes the data that is immediately necessary, other parts of the system can continue to function.
Conclusion
Developers should be aware of these key takeaways about edge computing:
- Edge is growing and will continue to evolve in the future.
- You can apply your knowledge of the cloud to edge computing concepts.
- Edge can benefit companies financially by improving efficiency and data security.
Edge is becoming a must for all in order to be successful. Developers are now in a position to capture the opportunity of edge. To learn more about how you can work with edge, visit our edge computing topic page.
Last updated: May 30, 2024