Builds for OpenShift provides developers with a consistent and secure way to create container images directly within Red Hat OpenShift clusters. With its foundation built on Shipwright, an open source CNCF project, Builds for OpenShift simplifies the process of creating OCI-compliant images using the image build of your choice while leveraging OpenShift's enterprise-grade capabilities.
Builds for OpenShift 1.2 is now generally available! This release introduces new features designed to enhance usability, broaden platform support, and enable developers to use Builds in a wider range of environments.
What’s new in Builds for OpenShift 1.2
The 1.2 release of Builds for OpenShift focuses on extending the product’s usability across diverse environments and architectures while continuing to improve the user experience of building container images on the platform. Let’s dive into the highlights.
Support for air-gapped environments and restricted networks
Many organizations run their container infrastructure in disconnected environments where clusters do not have full access to the internet due to the security requirements. With the 1.2 release, admins can take advantage of OpenShift mirroring procedure for disconnected clusters in order to install Builds from the OperatorHub and enable developers to run image builds within these clusters.
Support for Arm and IBM Power and Z systems
Red Hat OpenShift is supported on a diverse range of architectures and infrastructure including x86, Arm and IBM Power, and Z systems. With the 1.2 release, Builds for OpenShift is available on all architectures that the OpenShift platform supports
Shipwright Builds in Web Console
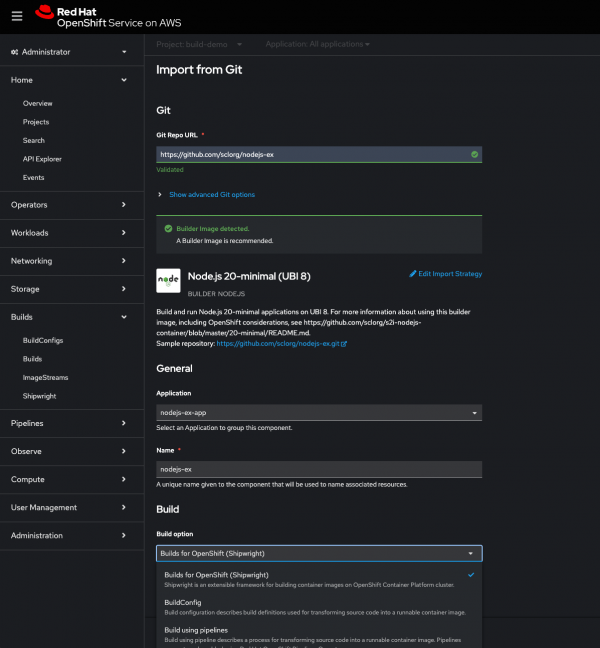
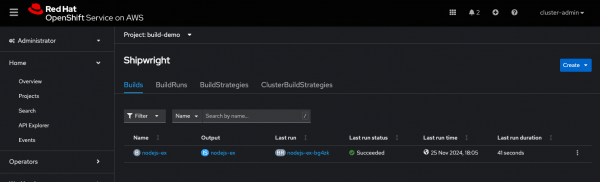
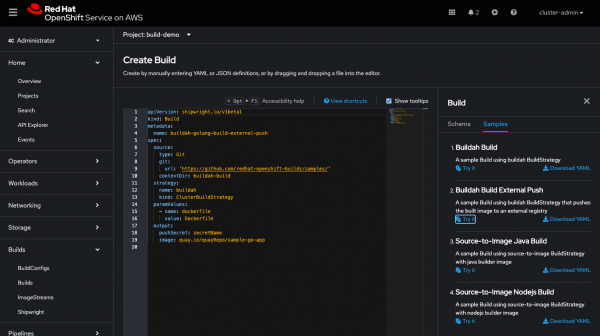
In order to simplify application onboarding with Shipwright, developers can choose to build their application with Shipwright Builds when importing it within the OpenShift Web Console. A Shipwright Build is then generated for the application to build an image and push it to the image registry. Furthermore, the Shipwright views are enhanced to provide easy access to Shipwright resources such as Builds and BuildStrategies in addition to including Build samples within the YAML editor to assist creating new Builds based on the provided examples.
Entitled builds with Shared Resource CSI Driver
Shared Resource CSI Driver enables sharing secrets and ConfigMaps across namespaces while controlling granular access through Kubernetes RBAC. This is particularly useful when building container images using a Dockerfile to install Red Hat Enterprise Linux (RHEL) RPM packages during the build which require an active RHEL entitlement configured. Using the Shared Resource CSI Driver, a cluster admin could allow specific namespaces to mount the RHEL entitlements (included in an OpenShift subscription) secret which is available on the cluster directly into the Shipwright Builds, Tekton Pipelines, and etc. and install RHEL RPM packages during Dockerfile builds. See below:
kind: SharedSecret
metadata:
name: etc-pki-entitlement
spec:
secretRef:
name: etc-pki-entitlement
namespace: openshift-config-managedOnce the admin has created the SharedSecret for the RHEL entitlements secret and configures RBAC for the target namespaces, developers can create Builds that consume the RHEL entitlements during the image build, without having to duplicate them into their namespace:
kind: Build
metadata:
name: myapp
spec:
...
strategy:
name: buildah
kind: ClusterBuildStrategy
volumes:
- csi:
driver: csi.sharedresource.openshift.io
readOnly: true
volumeAttributes:
sharedSecret: etc-pki-entitlement
name: etc-pki-entitlementGetting started with Builds
Builds 1.2 is available in the OperatorHub on OpenShift 4.12 to 4.17. In order to try Builds, install the Builds for OpenShift operator from the OperatorHub. Once ready, follow this guide to build an image using one of the provided build strategies. You can read more about this release in the documentation.
