Red Hat OpenShift Virtualization provides the ability to run virtual machines (VMs) alongside containers in a Kubernetes-native way. One of the key components enabling this is a NetworkAttachmentDefinition (NAD). NADs allow multiple network interfaces for VMs, enabling hybrid connectivity, virtual local area networks (VLANs), and high-performance network scenarios.
A NAD is a Kubernetes CustomResourceDefinition (CRD) used to define additional network interfaces for pods or virtual machines. The Multus CNI plug-in, integrated with OpenShift Virtualization, makes this possible.
Key features of NADs:
- Multi-networking: Ability to attach multiple networks to VMs.
- Custom networking: Define virtual local area networks (VLANs), single root input/output virtualization (SR-IOV), or MacVLAN configurations.
- Flexible IPAM: Use DHCP, static IPs, or other methods for IP allocation.
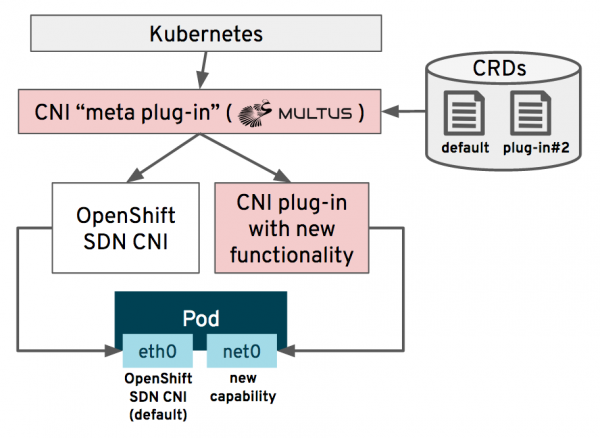
NAD architecture in OpenShift Virtualization
To better understand how NADs work, let’s break down the architecture, as shown in Figure 1.
- Primary network: Default OpenShift SDN.
- Multus CNI: Manages secondary networks and interfaces.
- Plug-ins: Specific configurations for MacVLAN, SR-IOV, or other setups.
How to create and use NADs
Let’s walk through a few examples of creating network attachment definitions.
Example 1: MacVLAN NAD configuration
This example sets up a MacVLAN-based secondary network for a VM. MacVLAN is often used to segment traffic within the same physical network.
YAML: MacVLAN NAD configuration
apiVersion: k8s.cni.cncf.io/v1
kind: NetworkAttachmentDefinition
metadata:
name: macvlan-network
namespace: my-namespace
spec:
config: '{
"cniVersion": "0.3.1",
"type": "macvlan",
"master": "eth0",
"mode": "bridge",
"ipam": {
"type": "static",
"addresses": [
{
"address": "192.168.1.100/24",
"gateway": "192.168.1.1"
}
]
}
}Attach MacVLAN NAD to a VM by adding the NAD to your VM specification under networks and interfaces:
apiVersion: kubevirt.io/v1
kind: VirtualMachine
metadata:
name: my-vm
namespace: my-namespace
spec:
template:
spec:
domain:
devices:
interfaces:
- name: default
masquerade: {}
- name: macvlan-net
bridge: {}
networks:
- name: default
pod: {}
- name: macvlan-net
multus:
networkName: my-namespace/macvlan-networkExample 2: SR-IOV NAD configuration
SR-IOV provides near-native network performance by dedicating a virtual function (VF) from a physical network interface controller (NIC) to a VM.
YAML: SR-IOV NAD
apiVersion: k8s.cni.cncf.io/v1
kind: NetworkAttachmentDefinition
metadata:
name: sriov-network
namespace: my-namespace
spec:
config: '{
"cniVersion": "0.3.1",
"type": "sriov",
"ipam": {
"type": "host-local",
"subnet": "192.168.2.0/24",
"rangeStart": "192.168.2.100",
"rangeEnd": "192.168.2.200",
"gateway": "192.168.2.1"
}
}Attach SR-IOV NAD to a VM and update the VM specification to include the SR-IOV interface:
apiVersion: kubevirt.io/v1
kind: VirtualMachine
metadata:
name: sriov-vm
namespace: my-namespace
spec:
template:
spec:
domain:
devices:
interfaces:
- name: default
masquerade: {}
- name: sriov-net
bridge: {}
networks:
- name: default
pod: {}
- name: sriov-net
multus:
networkName: my-namespace/sriov-networkExample 3: VLAN configuration
VLANs allow logical segmentation of networks, which can be configured using Multus and a VLAN container network interface (CNI) plug-in.
YAML: VLAN NAD configuration
Last updated: January 16, 2025